How to keep the company information secure when working remotely.
June 19, 2020 12:33 pm | by Aviral Chitkara | Posted in Business Management
Almost a month ago, a couple of people in my organization received emails from the Director stating some important discussion along with a link in the mail body. However, the people who received the email were in regular touch with the Director and could make out it was not his email style. This raised suspicion, and on checking the email address they found that it was from a fake ID. An alert was issued to the entire team to practice caution over such emails. Due to our stringent and well-implemented IT security practices, it was not something of huge concern for us.
This incident got me thinking. The concept of remote working is not an experienced territory for many organizations. Before the COVID pandemic, employees used to take WFH once or twice in a couple of months. Nobody was prepared for this kind of ‘new normal’ that companies and teams are currently experiencing. And this lack of know-how has exposed them to extreme levels of cyber threats.
Today I will share things that you must do to keep the company and its sensitive information secure during the work from home tenure.
- Identify and alert the team about phishing attacks: The example I shared above fits this category perfectly to the T. Phishing attacks happen over email where the hacker baits you to click on the link under the pretext of it being some important document or link to some charity, etc. On the surface, these emails seem safe and from a trustworthy source but are not. You can protect your system from such attacks by checking the email address and not just the sender name.
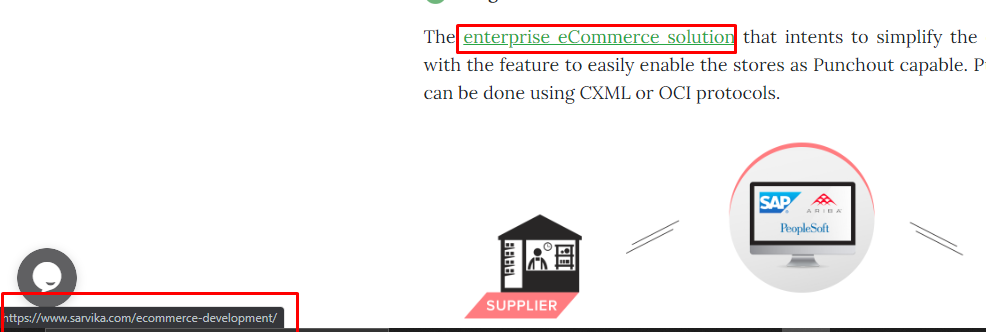
Another example is of domain spoofing, where the attacker impersonates to be someone else. A common domain spoofing technique is the blog post link. You may click on the link assuming it to be legitimate, but it gives the hacker access to your system information. You can check the linked page authenticity by simply bringing the cursor over the link (do not click) and the website address will be shown on the bottom left of the screen (as shown in the example above).
- Use end-to-end encrypted video-conferencing tools: Lockdown led to a sharp increase in the use of video-conferencing tools by companies and their teams daily. Leadership and top management also started holding such online meetings to discuss business decisions, financials, and other sensitive information. But soon a new problem cropped-up when hackers gained access to such meetings and leaked important data in the public. What is the solution? Using encrypted video conferencing tools that provide privacy and security. Most of the paid tool versions provide high-end encryption to protect your data. Avoid using free tools otherwise, you will compromise on the security.
- Limit the use of private devices: Many employees who used to work on dedicated PCs at their workplace are now connecting to the company system with their own devices. This practice can lead to a compromise in data security. Risks like an outdated version of antivirus software, saving files from online servers on the hard drive, lack of system protection, access to personnel other than the employee, etc. exists. The best way to tackle this scenario is by replacing personal devices with company-issued systems or make it mandatory for the employee using a personal device to access the network via a VPN.
- Higher levels of authorization protocols: Employee work stations and devices are constantly monitored at the premises. The same is not the case when people are working from home. This calls for stringent and more robust access controls to ensure there is no data spill-over. Practices like multi-factor authentication, powerful system passwords, firewalls, etc. must be used. Many organizations also implement the ‘least privilege’ policy under which every employee receives the minimum level of network access that is required to finish the job and achieve results.
- Outline an ‘IT Network and Security Policy’: Remote working will remain around until the doctors are able to find an effective cure against the virus. It means that working across every industry will happen using technology. Hence, the need arises for an IT Network and Security Policy that highlights the duties and responsibilities of the company, management, and employees for making remote working safe and secure. Such a policy comes handy in case the company faces any lawsuit for data leakage during the remote working period.
- Monitor employee activities: Technology has made it possible for you to monitor the team’s work, right from their total time to what they are doing on their systems. Make use of such software to not only safeguard sensitive information but also to maintain a healthy balance in the team working hours and task allotment. As a leader or a manager, you can track if an employee is working beyond hours, which in the short term may produce satisfactory results but can fireback in the long term.
Over to you.
I will not say that this list covers everything that will make work from home a hundred percent secure, but this list is sufficient enough for small to medium-sized companies. If your organization has offices in different cities within one country or around the world, then you have to consider more enterprise level of IT security.
I hope my blog was able to give you brief insights on how to make remote working secure. If there is something you would like to add, then mail me at hello@sarvika.com.
Written by Aviral Chitkara
Senior Business Operations Manager
Aviral is the Senior Business Operations Manager at Sarvika Technologies. His research skills are unquestionable, and so is his ability to provide constant motivation to the team. An engineer turned business expansion enthusiast, Aviral is a knowledge bank when it comes to politics. Whatever the confusion or problem, he is always the one with answers.